Why Lynx
We deliver GRC services as a value-driven framework to keep your business on track and operating efficiently
Trusted by the World’s Largest Enterprises to Small and Medium Businesses and Start-Ups
When it comes to securing the future of business, companies—from large enterprises to startups—turn to Lynx. We provide on-demand access to teams of experts, innovative approaches, and intelligent technologies. Our services empower customers to improve their overall security posture, achieve continuous compliance, and formulate risk-aware business strategies.
Our Core Services
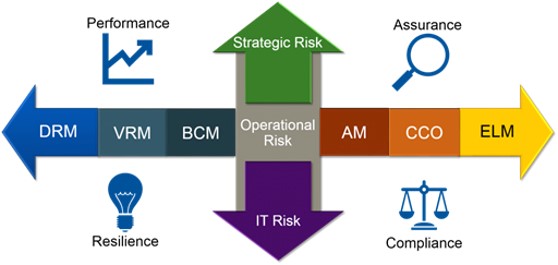
GRC
Streamline your end-to-end risk management processes or overcome specific cybersecurity obstacles with our GRC-managed services. We offer flexible access to the experts, tools, and resources you need to smartly balance GRC priorities.
Third-Party Risk
Whether you need help managing assessment backlogs and surges or running your end-to-end program, we provide services you can depend on to build, manage and execute a comprehensive Third-Party Assessment Program.
Risk Operations
Through our risk operations center (ROC), we enable next-generation CISOs and security organizations to define and deliver seamless risk management that improves operational effectiveness and efficiencies.
The Lynx Difference
We have earned the trust of companies in highly regulated industries worldwide. Here’s why.
On-Demand Ingenuity
Our dedicated team of security professionals has the training, experience and know-how to deliver adaptive security solutions that solve the unique challenges of your business and industry.
Value-Driven
From project start to finish, our team is invested in your success. We do whatever it takes to deliver cybersecurity and risk management as a value-driven business framework.
Agile & Adaptable
When requirements change, we respond at the speed of business. No matter the circumstances, we always aim to get the job done right, on time, and within budget.
Lean & Mean
We do not complicate our engagements with bloated project overhead or superfluous services. We’re here to deliver the solutions you need, as quickly, efficiently, and simply as possible.
Always a Step Ahead
Cybersecurity is a fast-moving target, so we move faster. We continuously innovate to deliver the resources you need to persevere through any challenge and secure a better future.
Dedication
We give you the attention you deserve. Our principals and seasoned professionals—not junior consultants—work directly with you through the full services lifecycle.
Our team holds the following Certifications and Clearances
- CISSP – Certified Information Systems Security Professional by ISC2 Certification
- ISSMP – Information Systems Security Management Professional by ISC2 Certification
- ISSAP – Information Systems Security Architecture Professional by ISC2 Certification
- ISSEP – Information Systems Security Engineering Professional by ISC2 Certification
- CAP – Certified Authorization Professional by ISC2
- C/EH – Certified Ethical Hacker by EC Council
- C/HFI – Computer Hacking Forensic Investigator by EC Council
- C/CISO – Certified Information Security Officer by EC Council
- CISA – Certified Information Systems Auditor by ISAC
- CISM – Certified Information Security Manager by ISACA
- CRISC – Certified in Risk and Information Systems Controls by ISACA
- NSA-IAM – National Security Agency InfoSec Assessment Methodology
- PMP – Project Management Professional by PMI
- GSLC – GIAC Security Leadership Certification
- CICM – Certified International Configuration Manager by CMTF
- CISCM – Certified International Software Configuration Manager by CMTF
- GSLC – GIAC Security Leadership Certification by SANS Institute
The Latest from Lynx
-

-
 Cybersecurity Governance Is All the Rage!governance risk
Cybersecurity Governance Is All the Rage!governance risk -
 Expert Advice to Protect Your Privacy Onlinecybersecurity
Expert Advice to Protect Your Privacy Onlinecybersecurity -
 Are You Prepared to Deal with Third Party Threats? Ask Yourself These Questions.Third Party Risk Management
Are You Prepared to Deal with Third Party Threats? Ask Yourself These Questions.Third Party Risk Management -
 NICE Framework Success Story - Abstractcompetency
NICE Framework Success Story - Abstractcompetency -

-
 CORONAVIRUS: Another “Case” for Integrated Risk ManagementIntegrated Risk Management
CORONAVIRUS: Another “Case” for Integrated Risk ManagementIntegrated Risk Management -
 The ‘Culture’ of Risk Integration; When Integration Eats GRC for LunchIntegrated Risk Management
The ‘Culture’ of Risk Integration; When Integration Eats GRC for LunchIntegrated Risk Management -
 Third Party Risk Management: Just the Right Thing to DoThird Party Risk Management
Third Party Risk Management: Just the Right Thing to DoThird Party Risk Management -
 Third Party Risk Management: Is it just a fancy tool?Third Party Risk Management
Third Party Risk Management: Is it just a fancy tool?Third Party Risk Management -
 Cyber Security is Everyone’s Responsibilitycyber range
Cyber Security is Everyone’s Responsibilitycyber range -
 GRC Programs Largely Ignore Self-Destructing Risksgovernance risk
GRC Programs Largely Ignore Self-Destructing Risksgovernance risk -
 Are Your Cyber Warriors Combat Ready?cyber range
Are Your Cyber Warriors Combat Ready?cyber range -
 What is the Business Case for MSSP?cybersecurity
What is the Business Case for MSSP?cybersecurity -
 Practice Cyber Combat on a Cyber Rangecyber range
Practice Cyber Combat on a Cyber Rangecyber range -
 Healthcare Industry Case Study: Cybersecurity and Risk Managementcompliance mandates
Healthcare Industry Case Study: Cybersecurity and Risk Managementcompliance mandates -
 Risk Management Insights at the 2017 Shared Assessments SummitShared Assessments Summit
Risk Management Insights at the 2017 Shared Assessments SummitShared Assessments Summit -
 Five Ways to Reduce Your Audit Taxcompliance
Five Ways to Reduce Your Audit Taxcompliance -
 Vendor Risk Management: An Educational Webinar SeriesRisk Management
Vendor Risk Management: An Educational Webinar SeriesRisk Management -

-
 Escape Spreadsheet Hell: Transitioning Your GRC Effortscybersecurity
Escape Spreadsheet Hell: Transitioning Your GRC Effortscybersecurity -

-
 A Financial Services Cyber Security Resource GuideCybersecurity Talent Gap
A Financial Services Cyber Security Resource GuideCybersecurity Talent Gap