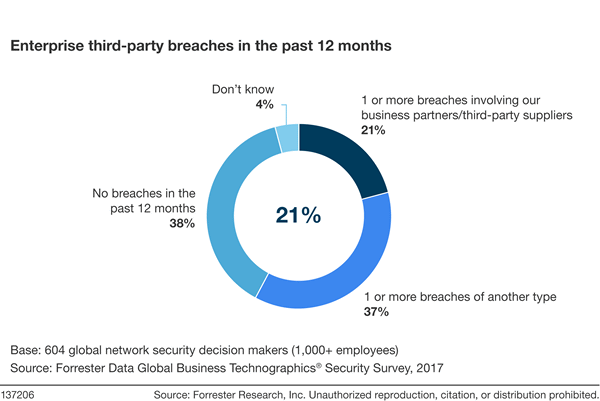
One-Fifth Of Enterprise Respondents Reported A Third-Party Breach according to Forrester’s Top Cybersecurity Threats of 2018.
Strategic Compromise Will Allow Attackers To Undermine Your Supply Chain
Your partners are also under threat: 21% of global enterprise network security decision makers have experienced a security incident involving a third party. Third-party risk is frequently discussed as an exposure due to data shared with partner companies and data processors. This type of downstream risk can sometimes put people in mortal danger as with the TigerSwan breach, where a third party leaked resume information for foreign nationals that included admissions of their complicity with US forces and home contact information. Too frequently, supply chain issues that are upstream to your organization are ignored and incidents go unnoticed and unpublicized.
- What you need to know: You may be drinking from a poisoned well. Forrester has been tracking a dangerous trend in which cybercriminals use compromised update servers to distribute malware, a trend that just this year has already affected Apple, IBM, and Google. This issue is particularly pernicious as it doesn’t require end user interaction, allowing attackers to deploy signed malware directly to your servers using trusted channels. The very channels you’re using to obtain security updates, cybercriminals are using against you.
- What you need to do about it: Perform threat assessments of your supply chain.This year, the US Department of Homeland Security (DHS) issued a directive banning the use of Kaspersky software by federal agencies. There has been a split in the security community, with some people questioning this decision and even demanding evidence of malfeasance. While Kaspersky has even gone to the effort of providing source code to vindicate themselves, the ability to push malicious updates has been discussed as an unacceptable risk. The decisions you make may not rival the global scale of this scenario, but you should be reviewing the amount of trust you place in suppliers and how seamlessly their software updates get deployed in your environment.
Read more about 2018 Cybersecurity Threats by Forrester. Download the report here.