Simply put, risk is the product of probablity times impact. A risk-based security strategy and IT Risk Management Program is created in order to make smart cybersecurity decisions that will enable the business to make the best cyber security investment and staffing decisions based on the probablity of an event, and the impact that event will have on the business operations.
The NIST Cyber Security Framework (CSF) was created in 2013 in response to the President’s call for an updated approach for dealing with cyber threats. He tasked the National Institute of Standards and Technology to collaborate with industry leaders and related stakeholders to develop the framework. I’d like to share some ideas on how you can use the NIST CSF framework to build an effective IT Risk Management Program for your organization.
The Role of Risk
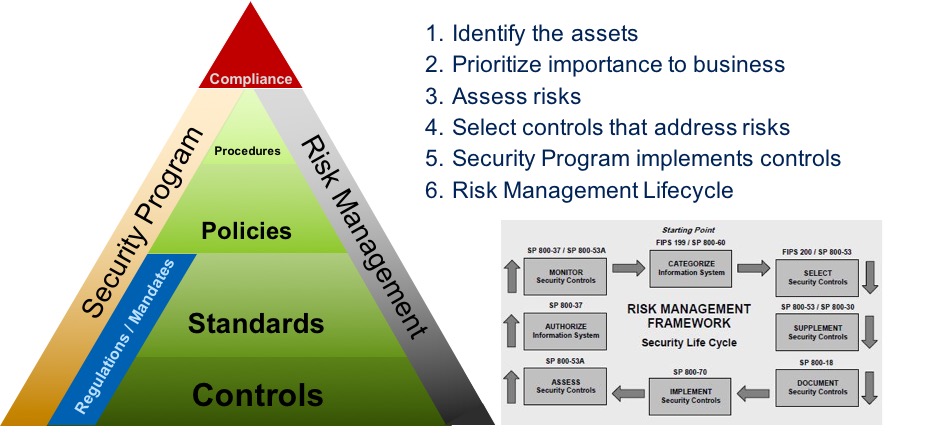
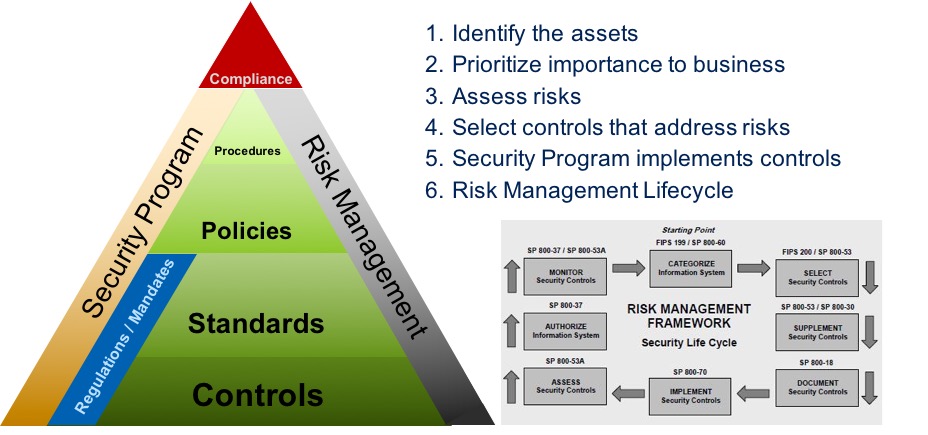
Security leadership is all about risk, since risk provides the context for your security program. After assessing risk, you must determine the controls that act as the foundation for the program; these controls are the activities created to enable your company to execute its business objectives, but they can’t exist in a vacuum — they are heavily impacted by a variety of regulatory guidelines, government statutes, your security posture, and even the threats your business may be facing.
Probability and Impact
When you assess cyber threats such as natural disasters, technical failures, external actors, internal resources, malicious code and hackers, you may find it tempting to think of risk in absolute terms. In practice, however, I find risk is defined by gray areas.
Risk is the product of 2 things:
Probability X Impact.
Probability is often qualitative in nature, while impact is normally quantitative – for example, how much money was lost as a result of a security breach. In simplest terms, you can even make an argument that the probability will approach 100% – It’s not if you are breached, but when. My suggestion is to rely on your experience and domain knowledge to make the best assessment for your particular circumstances. While considering qualitative and quantitative elements in estimating risk, remember to keep it simple.
Basic Structure
A neighbor built a new house recently. Over time, I watched it slowly change — the basic framework was created first, and different materials were then added to form the walls: stone cladding in the basement, wood and compound materials on the ground and upper floors. Likewise, the NIST CSF is a starting framework for managing IT Governance, Risk and Compliance (IT GRC). Use the security thought leadership resources in your company to help determine which elements you’ll include in your risk management program. The framework by itself will not solve your problems, but it is what you layer onto the framework that will give you the results you seek. To make getting started easier, the follow can be used as risk categories:
- Compliance (What happens if I fail to meet regulations?)
- Access Management (Who gets access to what?)
- Business Resiliency (Can I minimize impact?)
- Threat and Vulnerability Management (What’s coming after my systems and where do I have openings they can exploit?)
- Information Protection (What am I doing to protect my data?)
- Application Infrastructure (What am I doing to protect the systems my people and data are dependent on?)
I invite you to learn more by clicking here to download free resources that will help you apply the NIST CSF when creating your risk program.