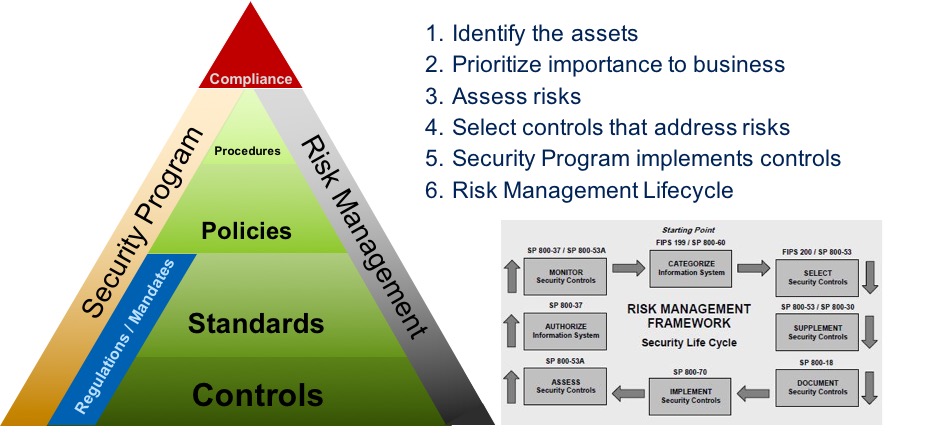
In today's digital age, cybersecurity has become critical for businesses of all sizes. However, companies need to demonstrate evidence of due diligence and due care for cybersecurity operations, which can be daunting without a proper framework. This is where The...