
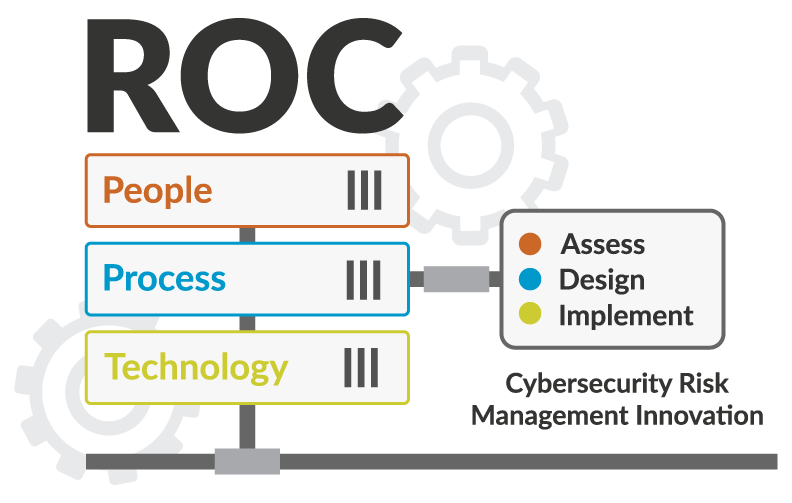
Risk Operations Center (ROC)
Lynx Managed Services are powered by our Risk Operations Center (ROC) and our risk intelligence and continuous compliance industry professionals to help define and deliver seamless risk management.
A Value-Based Approach to Risk Management
Reduce Risks
We reduce long time-consuming risk management activities by using technology to automate traditional and dated approaches to assessment and compliance.
Address Obstacles
Lynx Risk Operations Center (GRCaaS & TPRMaaS) addresses the obstacles in a constantly changing regulatory landscape and shortage of cybersecurity risk management expertise.
Deliver Security
We’ve positioned LRM and our LYNX ROC to address the high cost of delivering security and risk management processes.
Client Benefits
Gain Control.
Identification of control weakness and operational inefficiencies.
Assess Risks.
Ability to frequently or continuously assess risks through the timely consideration of transactions and/or operation of controls.
Problem Solve.
Increase ability to deal with issues when they are fresh and address problems before they escalate.
Organization Overview.
Gain a comprehensive view of the organization’s risk and compliance profile.
Lynx Risk Operations Center ROC Powered by LRM
Securing the Future with Seamless Risk Management
Lynx GRCaaS is powered by our Risk Operations Center (ROC) and our risk intelligence and continuous compliance industry professionals to help you define and deliver seamless risk management. This managed service enables the next generation CISO and security organization to improve operational effectiveness and efficiencies.
Shared and dedicated support models
Risk intelligence, analysis, and risk mitigation expertise
Use of Lynx Risk Manager to define and deliver program
Drive program efficiencies to achieve level 5 program maturity
Maintain policies and compliance documentation
Oversee and monitor risk posture
Provide proactive risk intelligence
Enable 360° GRC
ROC Setup
The Risk Operation Center is staffed by certified SMEs who provide risk management expertise and manage all aspects of the risk program. Identify and escalate compliance and management risks, execute assessments, and provide guidance on risk mitigation practices.
Risk Management Lifecycle
Lynx brings together the knowledge and technologies companies need to mature their GRC and ESG programs faster.
Lynx bridges the gap between security teams and executives/board members by translating risk exposure into measurable business impacts.
The Process
Align Goals With Security Objectives
Develop an Effective Governance Toolset
Operate Your Governance Program
Risk Operations ensures that business goals are achieved by evaluating stakeholder needs, criteria, metrics, portfolio, risk, and definition of value.
Risk Operations sets the direction of information security by delegating priorities and determining the decisions that will guide the organization.
Risk Operations establishes a framework to monitor performance, compliance to regulation, and progress on expected outcomes.
- Review BIA
- Data Classification
- Application Classification
- Governance Committee RACI
- Compliance Obligations
- Asset Classification
- Steering Committee Charter
- Information Security Policy Charter
- Policy Hierarchy
- Security Policy Framework Prioritization
- Policy Exception Handling Process
- Security-business alignment metrics
- Risk Register
- Security Awareness
- Compliance Monitoring
- Risk Assessments
- Tabletop Exercises
- Business Impact Assessments
- Risk Management
- Policy Development and Management
- LRM Management
- Third Party Risk Management
Align Goals With Security Objectives
Risk Operations ensures that business goals are achieved by evaluating stakeholder needs, criteria, metrics, portfolio, risk, and definition of value.
- Review BIA
- Data Classification
- Application Classification
- Governance Committee RACI
- Compliance Obligations
- Asset Classification
Develop an Effective Governance Toolset
Risk Operations sets the direction of information security by delegating priorities and determining the decisions that will guide the organization.
- Steering Committee Charter
- Information Security Policy Charter
- Policy Hierarchy
- Security Policy Framework Prioritization
- Policy Exception Handling Process
- Security-business alignment metrics
- Risk Register
Operate Your Governance Program
Risk Operations establishes a framework to monitor performance, compliance to regulation, and progress on expected outcomes.
- Security Awareness
- Compliance Monitoring
- Risk Assessments
- Tabletop Exercises
- Business Impact Assessments
- Risk Management
- Policy Development and Management
- LRM Management
- Third Party Risk Management

“Lynx Technology Partners showed us that we did not have to compromise when it came to our needs. When working with Water Quality Accountability ACT (WQAA), it is essential that the process is made simple to avoid confusion among those involved. Lynx helps with this by translating regulatory requirements into practical tasks and procedures, making it more understandable to everyone.”
Andrew Stravitz, CISO
Chief Information Security Officer





